Understanding Keyloggers 1
One day i decided to sharpen my C skills and get to implementing a keylogger. But then i found myself lost in a rabbithole of MSDN docs, Stackoverflow threads and other forums dating to 2002 or something… So i wrote this for whoever wants to learn more about how actually keylogging works so hopefully you won’t find yourself reading a 22 year old post ;) Please note that some concepts have been simplified for the purpose of this keylogger implementation....
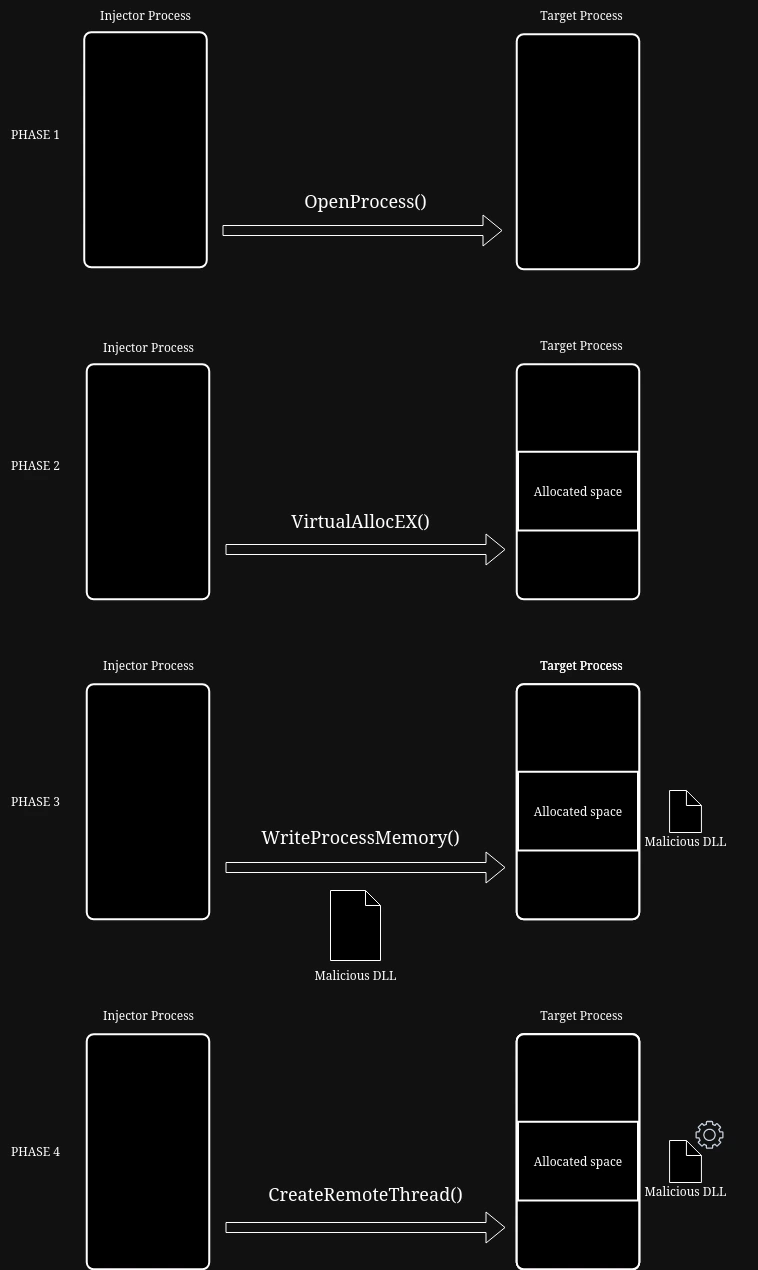
Injecting DLLs in C
Hey folks! It’s been a while since I last posted anything on the blog but we are back! and gonna be posting again regularly ;) I will explain as much as possible without going on a lot of tangents so further reading is always encouraged. Of course this is for educational purposes only blah blah. DLL Injection??? DLL injection is a “sneaky” way to insert our code in the address space of the target process thereby executing our code!...
WannaCry Challenge
Hey everyone! This challenge marks the end of the PMAT course challenges. I honestly learned a lot from this challenge, especially from the infamous WannaCry ransomware. I hope you learn as much as I did from this challenge! let’s get started Challenge Link 1. Record any observed symptoms of infection from initial detonation. What are the main symptoms of a WannaCry infection? Well the obvious symptom that the files on the harddisk start to have a ....
SillyPutty Challenge
Hello everyone! I’ve gotten great feedback about the TCM PMAT course, so I decided to enroll in it. I’ve had this course sitting in my purchased courses list for quite some time now, so I finally decided to get right into it and it’s been awesome so far! In this write up I’m solving the first challenge in this course out of 3 and it was lots of fun so i hope you enjoy reading!...
Malware Traffic Analysis 3
Malware Traffic Analysis 3 Created: May 25, 2023 3:46 PM The Malware traffic analysis challenge aims to detect the malicious payload and gather the correct information about it to take necessary procedures. Analyzing network traffic and identifying security threats is a huge key to detect and respond to attacks. It also helps in understanding the techniques used by attackers, which in itself helps in setting up better security measures and policies....